Updated 12/10/18. Please note: this article contains affiliate links for businesses I use and love.
Powering 30% of all websites in the world (and growing!) and capturing almost 60% market share of all open source content management systems, there is no doubt about WordPress’ popularity.
But when it comes to popularity on the internet, there are often consequences. Because of its widespread use, WordPress has become a favorite target for hackers and attackers.
Did you know:
- There are roughly 91,000 attacks on WordPress every minute.
- During the worst WordPress security breach, over 18 million users were compromised.
- 73% of the 40,000 most popular websites that use WordPress are vulnerable to attack.
Many of these hackers use bots to automate the process of sniffing out vulnerabilities from your site. With this in mind, an attack isn’t necessarily personal, which is why even the smallest, under-the-radar websites get hacked. Once their bots find a viable entry point, hackers jump in and take advantage. If you’d like to learn more about ways cybersecurity works and how websites can be hacked, consider taking cybersecurity courses to gain a deeper knowledge on the subject.
Before going through the comprehensive WordPress security checklist I’ve put together to help you safeguard your website from the worst possibilities, let’s take a deeper look into some common WordPress security issues.
Jump Ahead to a Specific Section:
What Hackers Can Do to your WordPress Website
WordPress Security Checklist: How to Protect Against WordPress Security Issues
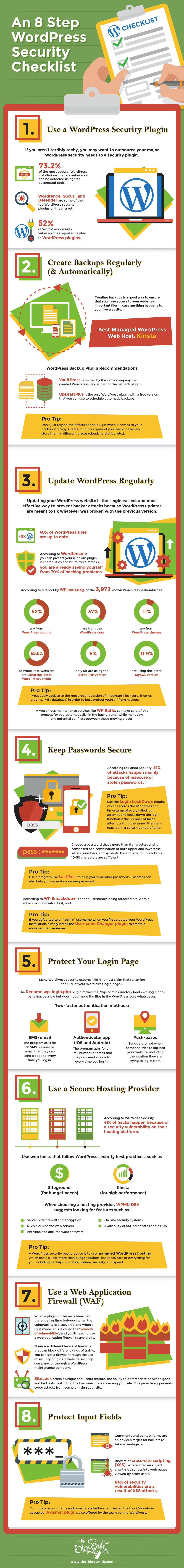
#1: Use a WordPress Security Plugin
#2: Create Backups Regularly (& Automatically)
#3: Update WordPress Regularly
#6: Use a Secure Hosting Provider
#7: Use a Web Application Firewall (WAF)
Final Thoughts: An 8 Step WordPress Security Checklist for WordPress Security Issues
What Hackers Can Do to your WordPress Website
According to the 2017 Cybersecurity Report by ISACA, 53% of enterprises experienced more attacks this year than the year prior. This is supported by research from Symantec, who found that ransomware attacks increased by 37% in 2017.
Here are some of the most popular reasons (and resulting impacts) for hacker activity on a website:
- Website vandalization. Hackers do this to make a name for themselves while hurting your brand.
- Overload web servers. Also known as DDoS attacks (distributed denial of service), this happens when hackers overload your site’s bandwidth or resources with a lot of hits, using one (or multiple) servers. It can also be considered as an act of vandalism.
- Spread viruses. Did you know that hackers can use your WordPress site to spread viruses and malware? They can do this by inserting malicious code in the backend, or by uploading files for download on the site’s frontend.For example, just last year, hackers took advantage of the BlogVault plugin to infect its users with malware. The four most common WordPress malware infections are backdoors, drive-by downloads, pharma hacks, and malicious redirects
- Inject malicious content. Not all hacking happens through the backdoor of your website. Sometimes, hackers will focus on posting links to malicious websites in hopes that your website’s visitors click on them. There are a few different ways to do this, such as comment spam, spam contributions, and hacking into your email and sending spam messages to your followers.
- Host pages from your server. Hackers might construct an attack against you that involves either legit or phishing pages from your server. The latter is used to collect information from website visitors, and can be done by inserting a contact form which directly collects sensitive information. Alternatively, hackers can redirect visitors to another website where they can collect the information. Google blacklists 50,000 websites daily for phishing.
- Steal server bandwidth. Hackers can do this through hotlinking, a method by which users direct link files (images, video, etc) so that it appears on their website despite being hosted on yours. By doing so, they use up your bandwidth to view the files that are hosted on your website. Some web hosts charge based on bandwidth used, so if you go over your monthly allotted bandwidth, your website is billed extra or taken offline.
- Steal information. Hackers can steal anything from user’s personal information to a business’ trade secrets, and either use it for their own purposes or hold it for ransom.
Pro Tip: Read more about WordPress security vulnerabilities on a recent article I wrote for GoDaddy.
WordPress Security Checklist: How to Protect Against WordPress Security Issues
Some of the weakest points of a website include passwords, input fields (like forms), comments, and payment gateways; WordPress database, core, themes and plugins, and even your WordPress hosting server.
This WordPress security checklist will help you to build protection for these weak points.
#1: Use a WordPress Security Plugin
If you aren’t terribly techy, you may want to outsource your major WordPress security needs to a security plugin.
73.2% of the most popular WordPress installations that are vulnerable can be detected using free automated tools. There are several plugins — like Wordfence, Sucuri, and Defender — that offer functionality that includes scanning for vulnerabilities, blocking security threats and malicious networks, implementing a firewall, and monitoring DNS changes.
Upon discovering these vulnerabilities, cleaning the website is the next task. Although some of the aforementioned security services offer cleaning services, the wait for external security personnel to clean your website can certainly be excruciating. MalCare Security Plugin is an automatic cleaner that allows website owners to clean a hacked site with a simple click of a button.
While we’re talking about WordPress plugins, it’s worth mentioning that 52% of WordPress security vulnerabilities reported related to WordPress plugins.
#2: Create Backups Regularly (& Automatically)
Creating backups is a good way to ensure that you have access to your website’s important files in case anything happens to your live website. Most web hosts will do this automatically in the background but make sure to double check with them before relying on this safeguard!
I recommend Kinsta for their performance WordPress hosting but the fact that they let you create multiple automatic/manual backups is just another reason to check them out.
There are several plugins that you can use to automatically create backups, but one of the most recommended options is VaultPress, which is owned by the same company that created WordPress (and is part of the Jetpack plugin). UpDraftPlus is another great option — the only WordPress plugin with a free version that you can use to schedule automatic backups.
Don’t just rely on the efforts of one plugin when it comes to your backup strategy. Create multiple copies of your backup files and store them in different places (cloud, hard drive, etc.).
#3: Update WordPress Regularly
Updating your WordPress website is the single easiest and most effective way to prevent hacker attacks because WordPress updates are meant to fix whatever was broken with the previous version.
Despite this fact, only about 40% of WordPress sites are up to date. WordPress automatically updates for minor fixes, but major updates like the WordPress 5.0 update must be manually initiated.
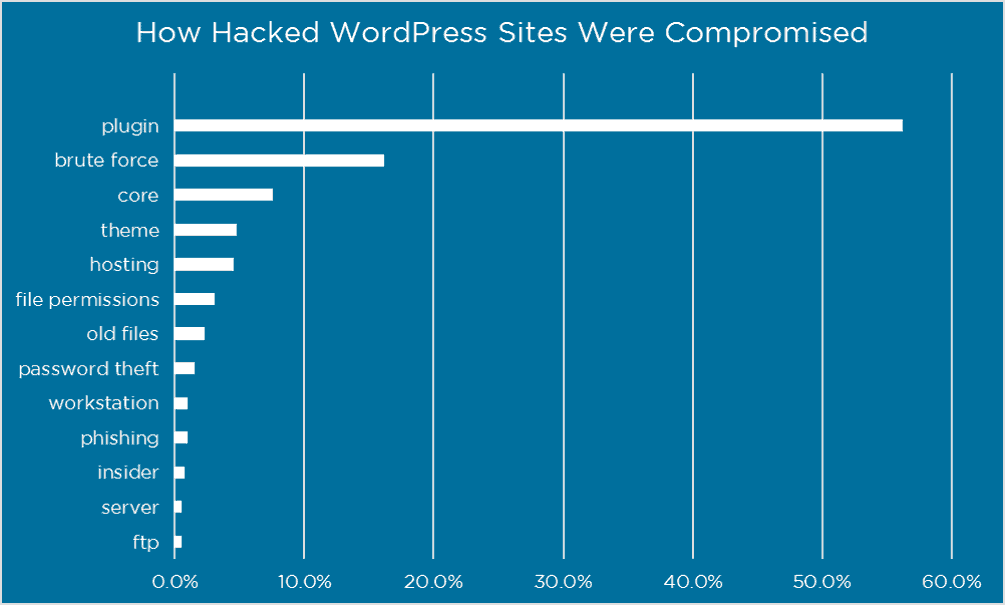
You must also ensure that along with timely WordPress core updates, your plugins and theme files are updated in a timely manner. According to Wordfence, if you can protect yourself from plugin vulnerabilities and brute force attacks, you are already saving yourself from 70% of hacking problems.
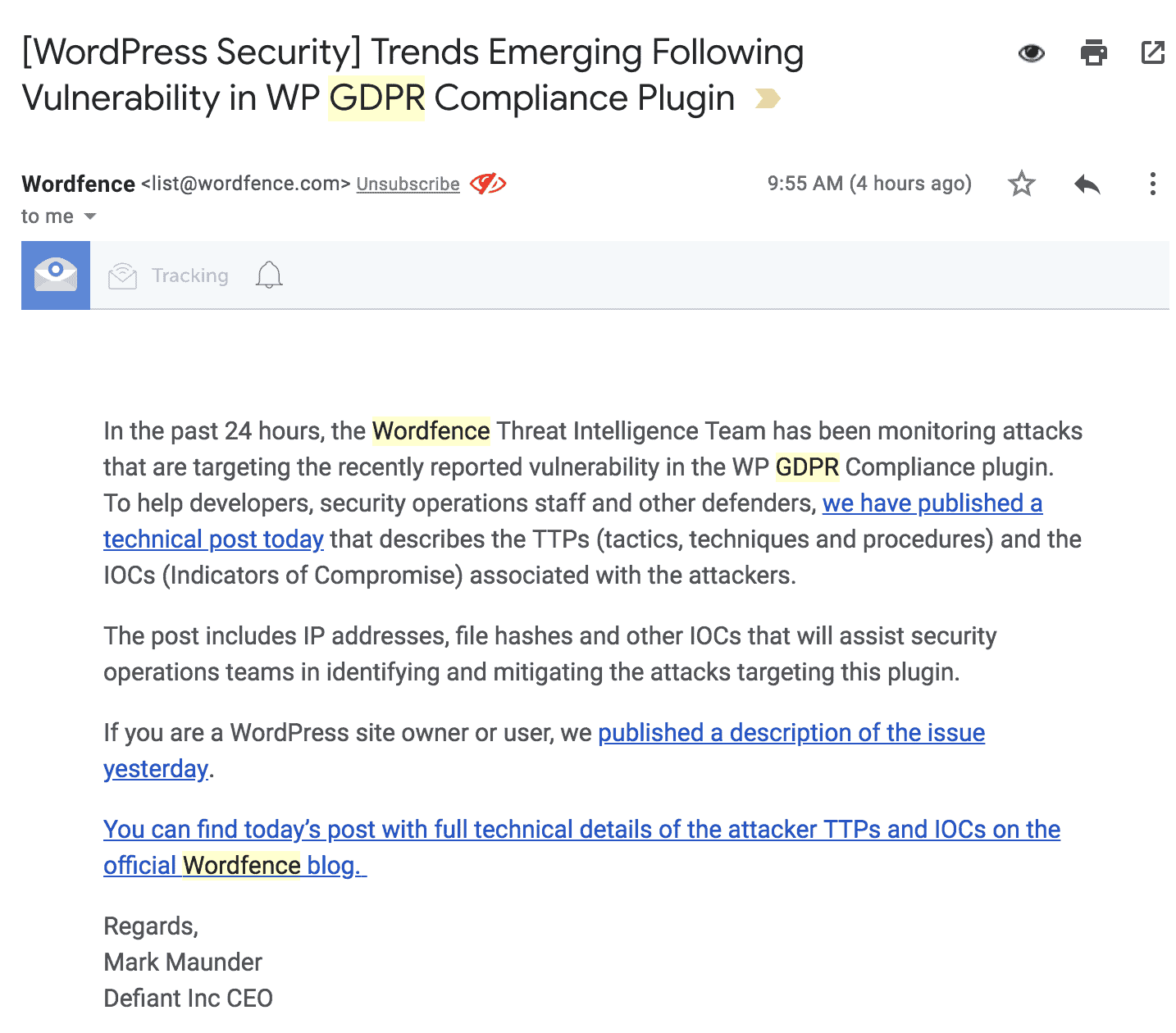
Speaking of Wordfence, you should sign up for their email updates. They send out timely and detailed warnings about the latest WordPress security issues.
Here’s one of their latest alerts:
According to a report by wpscan.org, of the 3,972 known WordPress vulnerabilities, 52% are from WordPress plugins, 37% are from the WordPress core, and 11% from WordPress themes. Finally, 65.6% of WordPress websites are using the latest WordPress version (4.9), but only 6% are using the latest PHP version (7.2), and 0.9% are using the latest MySQL version (10.2).
The major takeaway here regarding WordPress security issues? You need to proactively update to the most recent version of important files (core, themes, plugins, PHP, database) in order to best protect yourself from hackers.
A WordPress maintenance service, like WP Buffs, can take care of this process for you automatically, in the background, while managing any potential conflicts between these moving pieces.
When making major updates, there are rare occasions when you might get stuck in WordPress maintenance mode — but it’s not too difficult to get back on track.
#4: Keep Passwords Secure
Keeping your WordPress password secure is a given preventative security measure, but you’d be surprised at the number of people that are unable to adequately protect themselves from related attacks. According to Panda Security, 81% of attacks happen mainly because of insecure or stolen passwords.
A lot of attackers gain entry to your WordPress site via brute force — the repeated entry of username and password combinations until they get the right one. An easy way to prevent this possibility is by limiting attacks by limiting login attempts.
Pro Tip: Use the Login LockDown plugin, which records the IP address and timestamp of every failed login attempt and locks down the login function if the number of failed attempts from the same IP range is reached in a certain period of time.
Next, choose a password that’s more than 6 characters and is composed of a combination of both upper and lowercase letters, numbers, and symbols. For something uncrackable, 10-50 characters are sufficient. WordPress can also generate an almost-uncrackable password for you.
Pro Tip: Use a program like LastPass to help you remember passwords. LastPass can also help you generate a secure password.
On that note, change passwords often and don’t reuse passwords. It’s also advisable to use your email instead of username to log into WordPress because usernames are easier to predict than emails. According to WP Smackdown, the top usernames being attacked are: Admin, admin, administrator, test, root.
Pro Tip: If you defaulted to an “admin” username when you first created your WordPress installation, simply install the Username Changer plugin to create a more secure username.
#5: Protect Your Login Page
Apparently, I missed the new best practices claiming that renaming the URL of your WordPress login page is not helpful.
Or, so said the commenters on a related piece I wrote about WordPress security issues for WPKube:
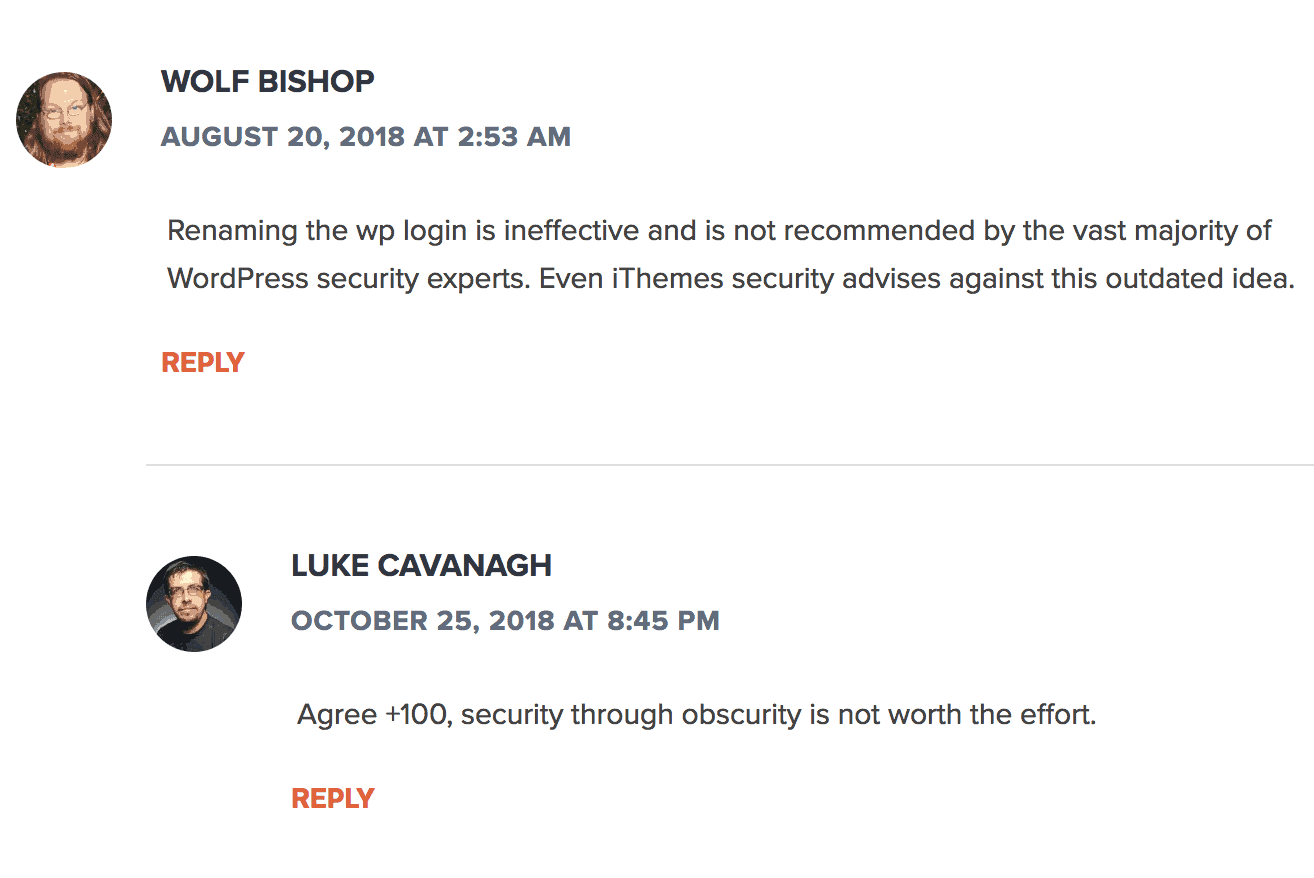
Regardless, I’ll share a related resource for the sake of being comprehensive.
The Rename wp-login.php plugin makes the wp-admin directory and wp-login.php page inaccessible but does not change the files in the WordPress core whatsoever.
At any rate, security through “obscurity”, as commentator Luke Cavanagh put it, certainly isn’t the only way to lock down your WordPress login page.
Another option? Implementing two-factor authentication (2FA) for logging in. This method requires registering/activating another device to confirm the site owner’s identity.
There are a few two-factor authentication methods:
- SMS/email. The program asks for an SMS number or email that they can send a code to every time you log in.
- Authenticator app (iOS and Android). Relies on time-sensitive one time passwords (OTPs) that are generated every period.
- Push-based. Sends a prompt when someone tries to log into your website, including the location they are trying to log in from.
Many of my clients use some type of two-factor authentication to lock down access to the backend of their WordPress blogs — I’d say it’s worth following their lead.
While two-factor authentication can be a fairly fool-proof method for beating some of the top WordPress security issues, it can certainly be a hassle — especially if you don’t have your phone with you (/if you can’t use cellular data while you’re traveling) or if you forget the email you used to sign up with.
Furthermore, using the Authenticator app means that you’ve authorized the specific device where you’ve installed the app. If you get a new mobile device, you’ll have to redo this process — ideally before you delete the data on your old device!
The risk of the SMS method in 2FA is the fact that you’re giving away private information that companies could potentially use to send you spam. Also, if hackers get ahold of your phone number, they can use this to gain access to your account.
If this situation seems unlikely, don’t forget about recent data breaches (Experian, Cambridge Analytica, etc.) on seemingly secure platforms.
#6: Use a Secure Hosting Provider
It’s worth mentioning that your hosting provider plays a role in keeping your WordPress site secure. In fact, according to WP White Security, 41% of hacks happen because of a security vulnerability on their hosting platform.
Depending on what you’re willing to spend, there are different types of web servers you’ll have access to through the average web host. Typical budget options usually revolve around the use of a shared web server. This means that you’re sharing the server resource with other users, making your website susceptible to cross-site contamination, where hackers can access your website through a neighbor on the same server.
Use web hosts that follow WordPress security best practices, such as Siteground (for budget needs) and Kinsta (for high performance). Both include access to SSL certificates that encrypt user’s personal data. Since HTTPS is now an official ranking factor, ideally, you’ll make sure that this security fix has been implemented ASAP (if you haven’t already).
Pro Tip: If you’re still using HTTP, follow along with my guide for switching to HTTPS for Pathfinder SEO.
When choosing a hosting provider, WPMU DEV suggests looking for features such as:
- Server-side firewall and encryption
- NGINX or Apache web servers
- Antivirus and anti-malware software
- On-site security systems
- Availability of SSL certificates and a CDN
A WordPress security best practice is to use managed WordPress hosting, which costs a little more than budget options, but takes care of everything for you including backups, updates, uptime, security, and speed.
#7: Use a Web Application Firewall (WAF)
When a plugin or theme is breached, there is a lag time between when the vulnerability is discovered and when a fix is made. This is called the “window of vulnerability”, and you’ll need to use a web application firewall to avoid this.
There are different levels of firewalls that can block different kinds of traffic. You can get a firewall through the use of security plugins, a website security company, or through a WordPress maintenance company.
I’ve been testing out SiteLock recently and it offers a unique and useful feature: the ability to differentiate between good and bad bots, restricting the bad ones from accessing your site. This proactively prevents cyber attacks from compromising your site.
Here’s my in-depth SiteLock review, if you’re curious about learning more.
#8: Protect Input Fields
Fields like comments and contact forms are an obvious target for hackers to take advantage of. They can steal data being entered to those fields by force or by stealth (like by monitoring keystrokes).
On a similar note, beware of cross-site scripting (XSS), where attackers inject client-side scripts into web pages viewed by other users. 84% of security vulnerabilities are a result of XSS attacks.
Pro Tip: Some websites receive tons of spam comments, which is why they choose to disable comments. However, comments are a great way of communicating and getting feedback from readers and visitors. To moderate comments and proactively battle spam, install the Akismet plugin, also offered by the team behind WordPress.
Visual learner? You’ll appreciate this WordPress security checklist infographic summarizing the major points of this post:
Final Thoughts: An 8 Step WordPress Security Checklist for WordPress Security Issues
The worst WordPress security issues are those that you haven’t proactively prepared for. Once the damage is done, it may be too late to protect sensitive data. Instead of waiting for the inevitable (at least according to statistics), use this WordPress security checklist to protect your website from the worst WordPress security issues. Once you’ve made it through, check out 24 Ways for some next level ideals to improve WordPress security.
Don’t have time to go through everything right now? You’re in luck! I’ve put together a one-page WordPress security checklist that you can download and save for later (or send to your web developer).












Thanks for stopping by to share your insights, Shiju!
Eventhough we secured our website in a proper way, the hosting providers server should be secure in order to completely we can say you are secure. As I can see past several years of Linux and Windows web server administration the hackers are going smart day by day. Even WAF, Immunify, CSF are the protecting tools for the servers and the series of IP attacks coming day by day.
Measures to take from webmaster side.
Ensure your wordpress security with updated plugins, WordPress, PHP, mysql.
Use wordpress security plugin paid will give you more protection
ensure the .htaccess file security itself
giving certain rules for protecting the folder inside wordpress
Remove unwanted plugins and themes
Monitor logs
Use CDN like cloudflare free version gives you total matrx of traffic
Backup the files in regular intervals
check the file changes time stamps in regular intervals
Disable theme edit via dashboard
user permission is always matters, carefuly do that.
change login url, uername, restrict the Json REST function for authorised users only. you can check this with the URL https://yourdomain.com/wp-json/wp/v2/users/1 ). You can see the username of your wordpress site which is insecure your site.
You can restrict this access by adding filters in https://Yourdomain.com/wp-content/theme//functions.php.
By shiju
A wordpress lover
Thanks Amos! My friends at Easel.ly made it 🙂
The infographic you used is very nice. Helpful article.
Martin –
I actually did not know that — thank you so much for the correction! I’ll make that change in the article.
– Maddy
Akismet is not free for commercial websites. So that would be the majority of sites on the web.